Imagine you are a forensic examiner, searching for key evidence that can lead you to the suspect of a crime. A likely place you would look for evidence is on digital devices, specifically information stored by apps on a mobile device. But how can you possibly keep up with the over 1.4 million apps available?
“It is highly unrealistic for any investigator to be familiar with all the apps. There is no way to have that kind of expert knowledge,” says CSAFE researcher and Iowa State University Professor of Electrical and Computer Engineering Dr. Yong Guan.
To solve this problem, a research team led by Professors Yong Guan and Neil Gong has developed an automated tool to analyze mobile apps like Snapchat or Instagram. “With our tool, the investigator doesn’t have to have expert knowledge about the apps. They just have to check our database to learn what types of evidence are available on the device,” Guan said.
Thus far, CSAFE researchers have analyzed 100,000 apps. “We hope to include all the apps from Google Play Store,” Guan said. “We are also continuing to analyze the apps available from other app stores to build a huge database that would be open to the crime lab investigators. The goal is to simplify their work and reduce the backlogs in those crime labs.”
The CSAFE research team led by Guan and Gong is taking a new approach that is improving on standard manual analysis, which may result in overlooking critical evidence. “Our automated mobile app analysis tool downloads a newer version of an older app or downloads a new app that we’ve never seen before and then runs on our modified Android ART platform, and then we run our analysis tool to collect data from the app and analyze it.”
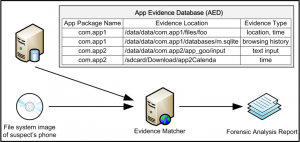
With this method, investigators are quickly able to uncover the types of evidence available, where the evidence is located, what format it is in, and other details such as a suspect’s location at a certain time.
“If a suspect drove from their home to a parking lot on the ISU campus, then walked to their office, there are multiple possible paths to take,” Guan said. “With the CSAFE mobile app tool investigators can reconstruct the paths people walk or drive to prove whether or not the suspect was at the scene of the crime.”
The CSAFE research team uses a dynamic program analysis approach, meaning that during analysis researchers run the app to learn what type of information is being generated. “We run the app on a real phone device (with a modified ART platform) and also we can run with what we call the emulator, a program running on the PC machine. We can run multiple emulators and within each of those emulators we can run multiple apps and speed up the analysis process.” This approach won the best paper award at the 12th IEEE International Workshop on Systematic Approaches to Digital Forensic Engineering in May 2018.
The CSAFE team has already established connections with law enforcement officials interested in implementing this technique. Researchers plan to expand their work to include evidence generated by text messages and remote servers and recovering digital information that users may have hidden. Learn more about CSAFE research in digital evidence on our research page.